May 03, 2023
Discover the Hidden World: Accessing I2P Darknet

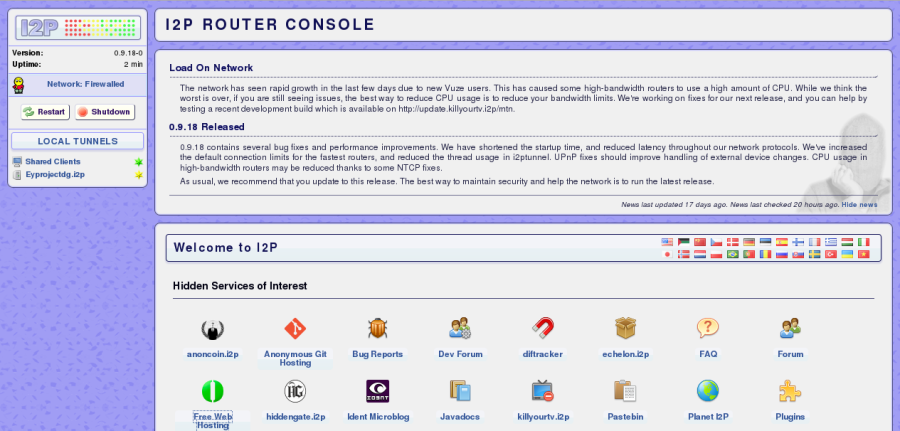
Retrieved from the archived blog, Get I2P, it should be noted that I2P darknet is not solely reserved for illicit activities. While it is true that I2PTunnel is an embedded application within I2P that facilitates communication between TCP/IP applications through set up "tunnels" accessible via predetermined ports on localhost, it is not the new hub for all things hidden and illegal online.
5 (1 278286. Screenshots via the author). The I2p darknet is a network that allows for anonymous communication and transactions. However, there is a growing concern surrounding the use of this network for illegal activities, such as the spread of ransomware. Ransomware is a type of malware that encrypts a victim's files and demands payment in cryptocurrency to decrypt them. This highlights the importance of cybersecurity measures and the need for individuals and businesses to protect their sensitive information.
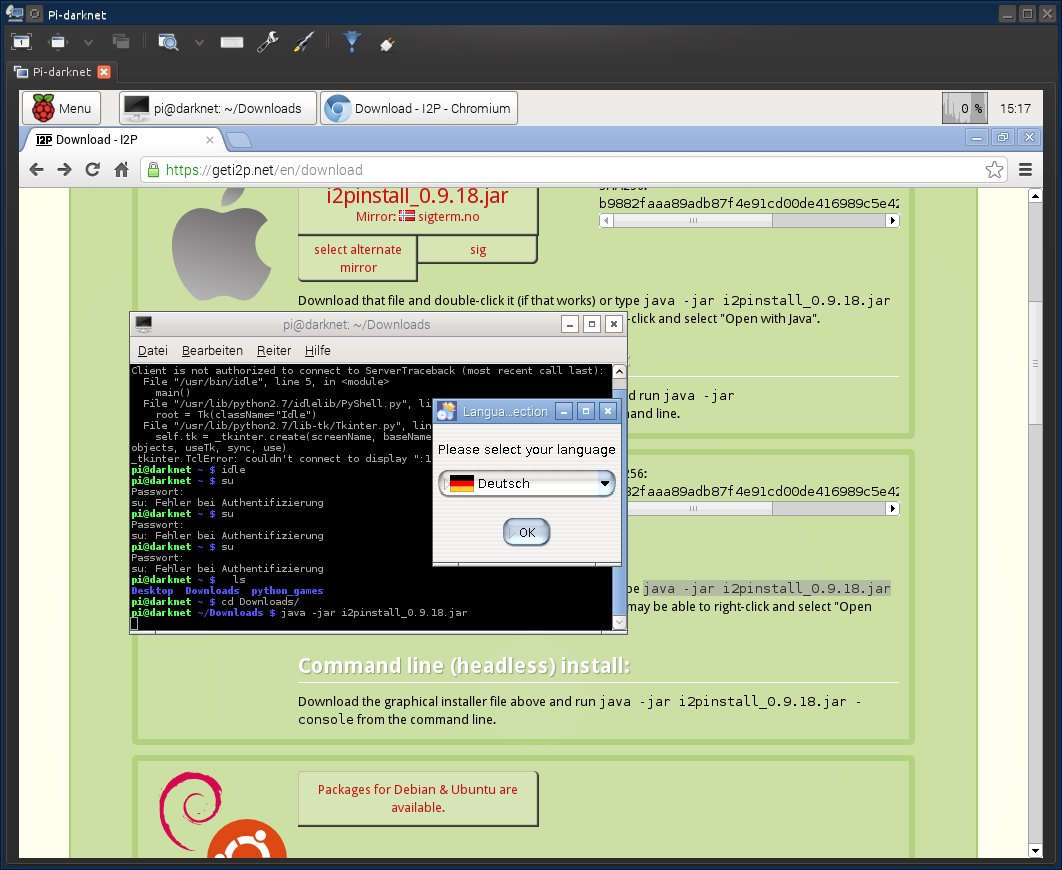
As previously mentioned, regular internet browsers are unable to access Tor servers due to their complete concealment. However, in 2017, a study was conducted to examine how forensic investigators could potentially exploit vulnerabilities in I2P software to gather valuable evidence. The study revealed that a seized machine running I2P router software may contain unencrypted local data that could be useful to law enforcement. In addition, a zero-day vulnerability was discovered for I2P in 2014, which was exploited to de-anonymize a minimum of 30,000 users. If you're looking to access the dark web, there are several ways to do so.
Discover the Secrets of I2P Darknet: Your Gateway to the Dark Web
The latest release, 0.9.30, of the I2p darknet software Syndie is focused on enhancing network resilience. Syndie is a tool designed to provide users with secure and anonymous communication through the I2p network. With the new release, users can expect improved reliability and stability when using Syndie. This is just one example of how the I2p darknet continues to evolve to meet the needs of its users for secure and private online communication.
The old version of I2P darknet,.9.44.9.44, is no longer maintained. However, it is worth noting that this version contains an essential fix for a denial of service problem in hidden services handling of new encryption types. It is important to keep in mind that this app operates differently from the official Tor browser, and even though it is a great option for iPhone users (as recommended by Tor Project), it may have potential vulnerabilities that are not found in the official Tor browser.
Recently, a zero-day broker took advantage dark web com of a vulnerability in I2P to uncover the identities of Tails users. This news highlights the importance of staying vigilant when using the darknet. On a brighter note, the I2PCon conference was a success, with its mission accomplished. The conference provided a platform for experts to discuss the latest developments in the darknet world.
While The Tor Project has the financial and legal infrastructure to support a network of exit nodes, I2P is not equipped with the same resources. As a result, I2P operates differently from Tor in this regard. This information was archived on September 15, 2015, and February 2, 2016.
If you're interested in the world of darknets, you may have come across I2P (Invisible Internet Project). I2P is a decentralized network that allows for anonymous communication and activity. It's often compared to Tor, another popular darknet network, but there are some key differences.
One of the main differences between I2P and Tor is the way they handle routing. Tor uses a series of nodes, or relays, to route traffic through the network. I2P, on the other hand, uses a distributed hash table (DHT) to route traffic. This means that there is no central point of failure, as there is with Tor. It also means that I2P is more resistant to attacks, as there is no way to shut down the network by taking out a few key relays.
Another key difference between I2P and Tor is the types of services they offer. While Tor is primarily used for accessing the dark web, I2P offers a wider range of services, including anonymous file sharing, anonymous chat rooms, and even anonymous email. This makes I2P a more versatile tool for those looking to stay anonymous online.
Of course, like any darknet network, I2P has its share of risks and drawbacks. Because it's decentralized and anonymous, it can be difficult to verify the trustworthiness of the people you're communicating with. There's also the risk of encountering illegal content or activities. However, for those who are willing to take these risks, I2P can be a powerful tool for staying anonymous and accessing a wide range of services on the darknet.
Discover the Secret World of I2p Darknet and Access the Hidden Web
I2P darknet has seen some changes with the latest version of SAM (v3.3). The previous version is no longer maintained. One notable feature of the new version is the use of QR codes to share hidden services, as well as identicons and router families. More information can be found by visiting zzz.
While I2P is not intended for anonymous browsing of mainstream websites like BBC or YouPorn, it has gained attention with the announcement of a new address for a popular dark market. I2P provides a secure platform for accessing private information stored on the cloud that cannot be accessed through traditional web browsing.
The I2P darknet is a free and open source project designed to create an anonymous network. This network allows users to communicate and share information without revealing their identity or location. By routing traffic through a complex network of nodes, the I2P darknet provides a secure and private way to browse the internet. Whether you are looking to protect your online privacy, access censored content, or simply explore the depths of the internet, the I2P darknet is a valuable tool for anyone seeking anonymity online.
IMule hasn't received any updates since 2013 and has been left without any further development. In the blog post titled "How to volunteer by helping I2P-Bote bootstrap", it's stated that the program is no longer being developed.
The latest stable version of I2p darknet is .6.1.6. This new update not only speeds up the transition to X25519 for routers but also allows for shorter tunnel build messages and better SSU performance. With I2p darknet, you can use any web browser as a proxy server.
Discovering the Active Darknet Markets on I2P Darknet
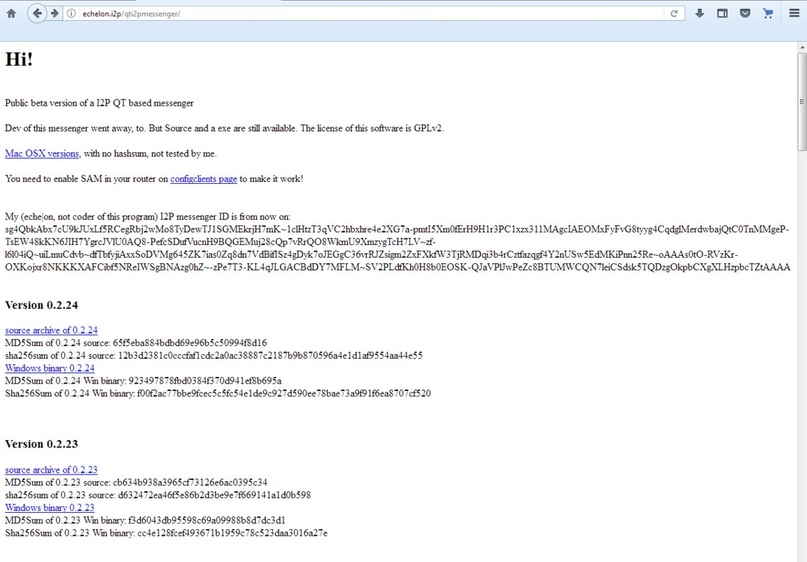
I2P-Messenger is a powerful tool for achieving complete anonymity during instant communication with people who may be strangers to the user. At the same time, it can also be utilized to have secure and untraceable conversations with close friends, family members, or colleagues. It is important to note that version 16 of I2P-Messenger is no longer maintained, but version.9 has critical fixes for XSS and remote execution vulnerabilities.
The I2p darknet is a network that provides anonymity to its users by routing their internet traffic through a series of encrypted tunnels. Although an older version of I2p is no longer being maintained, a newer version supports dark web cash app hack Debian Stretch and Ubuntu Zesty, with upgrades to Jetty 9 and Tomcat 8. Additionally, the new version also supports the migration of old DSA-SHA1 hidden services to the more secure EdDSA signature type. While some may associate the darknet with illegal activities, such as drug trafficking, the reality is that it serves as a platform for a variety of content, from Guardians of the Galaxy fan sites to political dissident blogs.
Explore further
Distributed by ibgatorbait7, LLC.